Exploring the World of SAST and DAST with a DevSecOps Twist
Defining SAST and DAST in Layman's terms for DevSecOps Professionals
Introduction
As a Cloud Security Engineer deeply immersed in the world of Application Security and DevSecOps, nothing excites me more than sharing my knowledge and passion for safeguarding applications against the myriad of cyber threats lurking in the digital world. In this blog post, we will embark on a fascinating journey through two pivotal concepts that keep your favorite apps secure: SAST and DAST.
What Exactly is SAST?
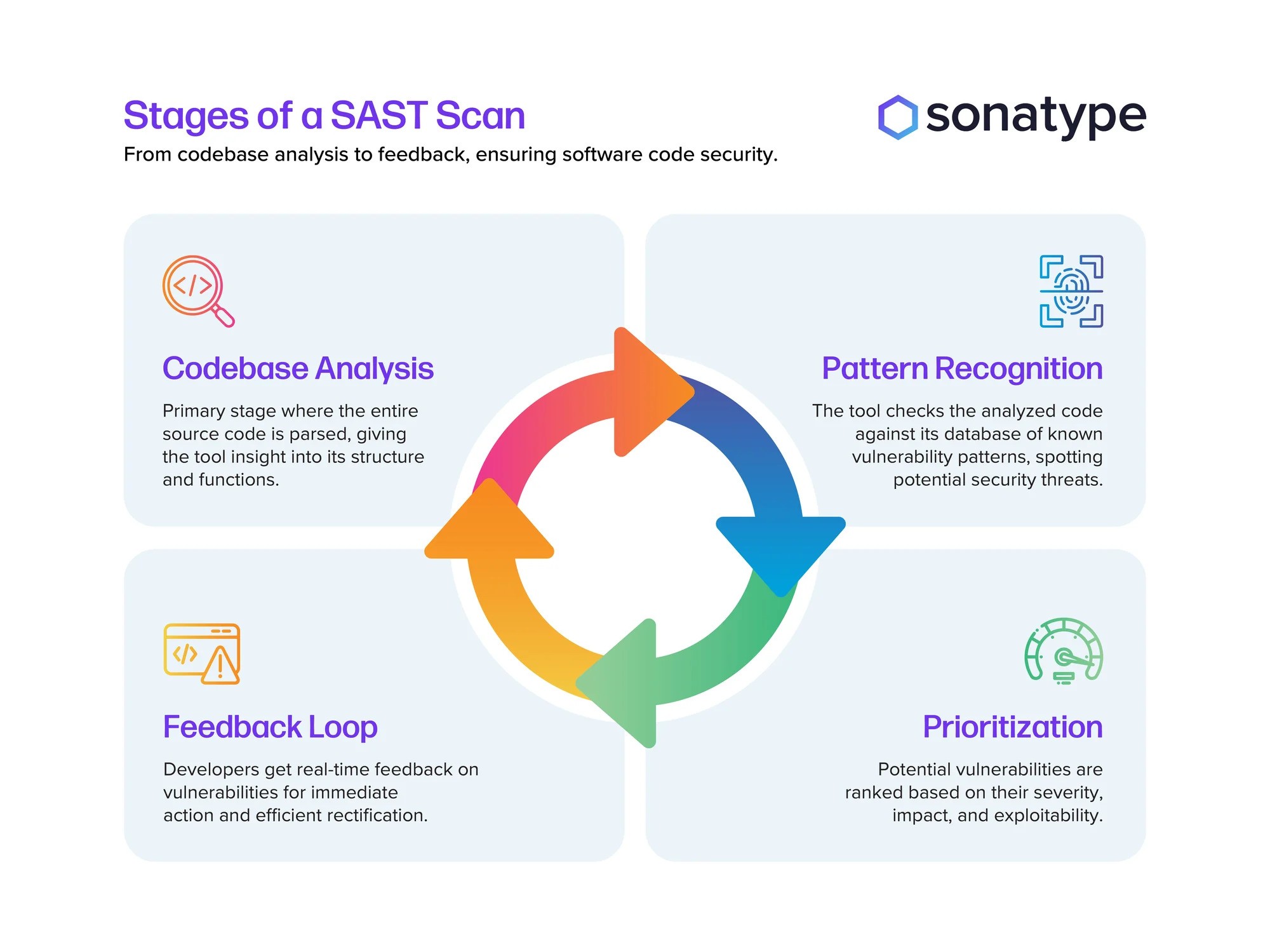
Imagine having a magnifying glass that lets you peer deeply into your application's source code, pinpointing vulnerabilities before they become a threat. That, my friends, is what I would call SAST. SAST, or Static Application Security Testing, involves a detailed analysis of an application's source code to identify any security weaknesses and vulnerabilities. The beauty of SAST lies in it's ability to detect these issues before the application is even compiled.
Figure 1: Stages of a SAST Scan by SonarType
To me, SAST equals static analysis. It's like having a preemptive strike capability within the Software Development Life Cycle (SDLC), allowing engineers to catch and rectify issues early on. This not only saves time but also fortifies the security posture before deployment or releases into lower environments. Moreover, integrating SAST tools into CI/CD pipelines automates security at a scale unimaginable a few years ago, making it a staple in modern development practices for robust application security.
Discovering DAST: The Dynamic Cousin
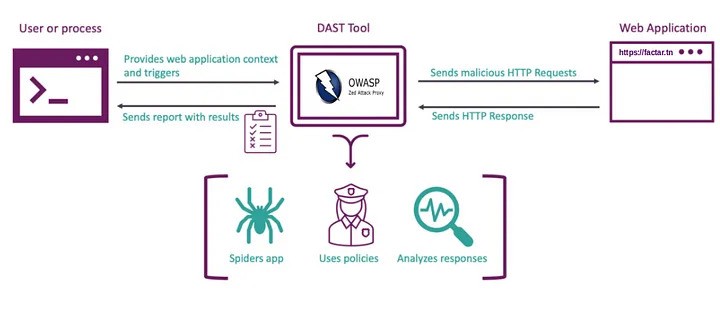
While SAST analyses the static aspects, DAST, or Dynamic Application Security Testing, brings in a dynamic perspective. It simulates live attacks on a web application, acting as a real-time assessment tool for identifying vulnerabilities in deployed applications. Think of DAST as the on-the-ground reconnaissance that validates the security measures by engaging with the application as an attacker would.
Figure 2: DAST Scanning Process
DAST shines by reducing false positives associated with SAST results due to its interaction with the live application. The findings are more accurate, providing actionable insights. Its comprehensive nature means it doesn't just stop at code; it looks at runtime environments, configurations, and external dependencies.
Key Differences Between SAST and DAST
Understanding the nuances between SAST and DAST can significantly impact how you approach application security. Therefore, I've taken the liberty of highlighting three key differences that you should know:
- Stage of Deployment: SAST is performed before compilation, early in the SDLC. DAST, on the other hand, is conducted on deployed applications, closer to or in the production environment.
- Scope of Analysis: SAST examines source code and static assets. On the other hand, DAST assesses the application's behavior by interacting with it in real-time.
- Nature of Testing: DAST offers a more realistic testing scenario by evaluating the compiled application in a runtime environment.
Incorporating both SAST and DAST in the appropriate stages of your SDLC enhances your application's security posture, ensuring a well-rounded defense mechanism against cyber threats.
When to Use SAST and DAST
For a secure web application, use SAST during the development phase and ensure it's a part of your CI/CD pipeline for continuous security. DAST should come into play later, ideally during the testing phase, to vet the application post-deployment. Integrating DAST into your release pipeline, with proper rollback strategies added, ensures that your security measures are not just thorough but also practical.
Tools of the Trade
Equipped with knowledge, let's talk tools. Based on my research and hands-on experience with SAST and DAST tooling, here are some recommendations:
For SAST:
- Checkmarx
- Fortify Static Code Analyzer
- SonarQube - (Open Source)
For DAST:
- Qualys Web Application Scanning
- OWASP ZAP (Open Source)
- Burp Suite (Open Source)
In addition to the ones mentioned, there are several other SAST and DAST tools that are available for various different services if you're interested in learning more:
Figure 3: DAST and SAST Tools/Frameworks
Wrapping Up
The ongoing battle against cyber threats necessitates a fortified defense, and understanding the strategic deployment of SAST and DAST methodologies provides a significant advantage. Remember, the goal isn't just to develop applications but to secure them in a manner that is both efficient and scalable.
I hope this deep dive gives you valuable insights into securing your applications. If you found this post helpful, please like, share, and subscribe. Your support fuels my passion, and I look forward to sharing more with you. Until next time, keep coding securely!
*Disclaimer: This blog post reflects my personal experiences and opinions.*
This blogs original content is based off of the following YouTube Video: